Last time I blogged about SSL and host-headers I was convinced it is only possible to host multiple SSL sites on one IP address when using a wildcard certifcate. I think I was right at the time, and now comes along Unified Communications UC SSL Certificates (aka Subject Alternative Name).
Same issue as before: host-headers enable you to host several websites on a single IP address. We run into a problem with several SSL certificates on one IP address. The first message a server sends in the SSL handshake contains relevant certificate, the server can only determine which certificate by IP address / port. If there is only one certificate to serve – no need to make a decision! Here we can serve a UC SSL certificate which is accepted by the web browser for multiple domain names.
I felt like trying this myself, extra curious to know what the certificate will look like in a browser. Managed to get this working in OpenSSL using a combination of two articles:
- Creating a Self-Signed Certificate using OpenSSL for use with Microsoft Internet Information Services (IIS) 5
- Creating a Certificate With Multiple Hostnames
Follow the steps for creating a CA in the first article. Grab the CA and import it into your IIS box. Switch over to the second article and add the changes to the openssl.cfg
[ CA_default ] copy_extensions = copy [ req ] req_extensions = v3_req [ v3_req ] # Extensions to add to a certificate request basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment # Some CAs do not yet support subjectAltName in CSRs. # Instead the additional names are form entries on web # pages where one requests the certificate... subjectAltName = @alt_names [alt_names] DNS.1 = stoniessl.info DNS.2 = freemegahost.info
Create a key for the multi domain certificate. Here we are skipping the “create CSR on IIS” step, and creating the key in OpenSSL.
openssl genrsa -des3 -out keys\multi.key 1024
Create a certificate request
openssl req -new -out requests\multi.txt -key keys\multi.key
Sign the certificate request
openssl.exe ca -policy policy_anything -cert certs\ca.cer -in requests\multi.txt -keyfile keys\ca.key -out multi.cer
Export the certificate AND private key (usually the private key would already be on in IIS box if you created the CSR in IIS)
openssl.exe pkcs12 -export -out multi.pfx -in multi.cer -inkey keys\multi.key
You now have a UC SSL cert you can install on the IIS box. By default IIS won’t allow you to enter a host-header when you are setting the SSL binding. There’s a little trick from this article: Using Host Headers and SLL in IIS 7 – give the certificate a friendly name starting with ‘*’!
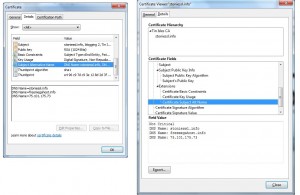
And what does the certificate look like? Here it is, in IE and FF:
Post a Comment